-
-
Notifications
You must be signed in to change notification settings - Fork 13
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Implement the IAB CCPA Compliance Framework #17
Comments
|
I think we should to this actually. Per today's final CCPA Regs, it is clear that technological solutions for opting out from the sale of personal information will be developed. Members of the IAB will probably implement the IAB approach. So, if our extension could hand this as well, that would be great. Probably, the fist order of business should be to find some example sites that are participating in the IAB approach. The Privacy String is technology-agnostic. So, how are people implementing this in practice? Ideally, it would be header-based solution as well. |
|
This also relates to the enhancement of the IAB CCPA framework. |
|
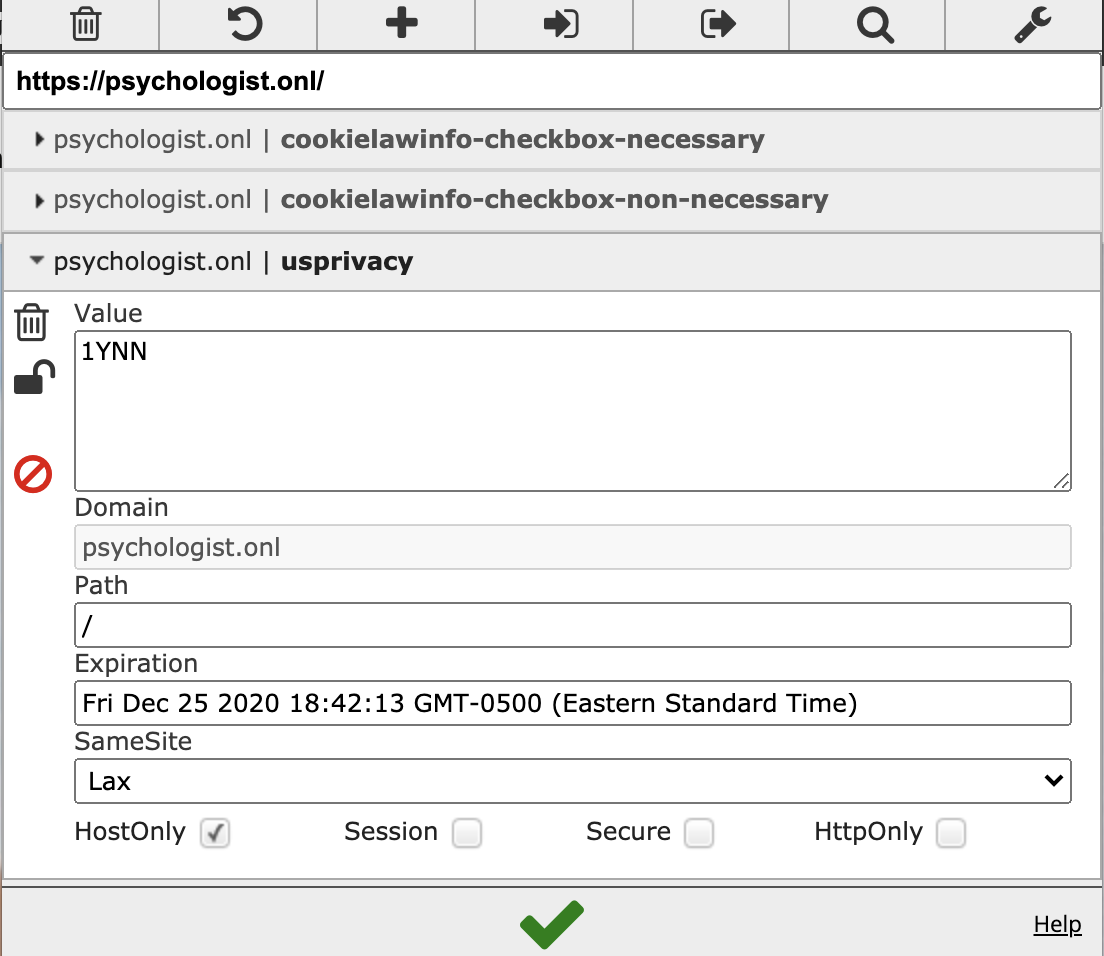
I thought about this some more. We should actually implement the Do Not Sell opt out functionality per the IAB CCPA framework. This will be the first real functioning opt out for all sites that make use of IAB CCPA framework. Here is the plan: The IAB Tech Lab U.S. Privacy String consists of four characters and is very similar to what we are actually doing. Here is an example: How the four character string is transmitted to the server is principally technology-agnostic. However, the IAB recommends storage in a first party cookie: What I am hoping is that our extension can identify the Here is a screenshot of using the EditThisCookie extension on https://psychologist.onl/ It would be great if we could automatically rewrite cookie values like this to, say, Now, this is probably a somewhat tricky task, especially, synching this with the whitelist (let's not worry about that for the time being). We may want to split this into multiple issues. For the time being, I am leaving this together, though. |
|
I started working on implementing the IAB CCPA guidelines for opting-out in our extension and managed to get a rudimentary cookie-modifier functioning. I haven't uploaded the code yet just because it is heavily based on how AccuWeather has implemented the framework (they have an 'opt-out' link in the site footer that links to a A few notes
Basically, it says a
To me it looks like this is an arbitrary choice on AccuWeather's part, though there could be some other reasons they set the domain this way that we don't know about. When I implement this I can just make sure to make a note of how a given site handles its cookie domain somewhere so that we only ever have one copy of the OverallIn general, the notes above are for future reference so my thought process on how to implement the IAB proposal is documented somewhere. @SebastianZimmeck, I will start to generalize this implementation and break it up into more fleshed out and manageable chunks over the next few days. Let me know what you think about what I have found. |
If it is not straight copied, it is OK in terms for copyright. You can certainly use the same APIs and the code can look similar.
If it is not a drag on performance, that would be OK. Maybe, it is possible to identify request with a cookie. The function would only need to be run for that. The points you describe with the
Sounds good. Generally, this looks promising to me. |
Maybe I misspoke when I said this. What I meant is that since AccuWeather does set and use the The rest does look promising, hopefully this is the right way forward! |
|
A few more sites that can be used for testing as they are using the IAB CCPA Compliance Framework.
Here is a site that lists various other domains having the usprivacy cookie. It does not seem to be always correct, though. |
|
The recent commit I pushed has functionality for sending a chosen cookie to every single site visited by a user. So far, there is no implemented functionality to check if a cookie is already on the site, and if there was one, for it to be parsed and responded to accordingly. I will continue to work on this alongside my suggestion below as well as issue #42. @SebastianZimmeck, after reading your updates to issue #42, I was thinking that we could use the idea of storing known ad networks' cookie profiles to a JSON and extend it slightly to allow us to store known variations of the |
Good idea. Per the IAB specification, it should be At the moment, I am thinking that it may be the best if you are creating two different JSON specs; one with the variations of the |
|
In the newest code update, I added:
What we need to work on next is handling the case where multiple cookies exist in the browser for some reason. Our extension avoids creating new cookies on AccuWeather, however this is not true for system.jobboard.io. When there is no cookie set and the page is loaded, the extension seems to get the opportunity to set its own before the site does, and the site apparently does not recognize the one we set by then. This can be seen here: Despite this needed fix, it seems like the core functionality is in place! I will continue to test this while I work on other parts of the extension, since it seems there will be a few minor bugs that will need to get worked out. |
So, our cookie is set on the domain,
As I see it at the moment, I do not think that it is a big problem that there are cookies in the domain and subdomain(s). Especially, if the site relies on setting and reading the cookie from multiple (sub)domains (not sure, is that the case?), it may be even necessary to have multiple cookies. If we can figure out exactly where the cookies are set and read, we can delete it. If we are not quite sure, I think it is OK to have multiple cookies. What would be important, though, is to have consistent values for these cookies. |
No, our cookie is the one set to the subdomain Fundamentally, it looks like this is the problem yes. You need to keep the name and the domain the same to overwrite a cookie. This is how our extension overwrites the cookie if It is important to note that in this case, the site-assigned IAB cookie's name is different than the one we assigned. This fact alone necessitates some kind of check for multiple cookies aside from the cookie domain issue.
This doesn't seem to be the case. Multiple cookies are set because whoever runs the given website doesn't check to see if another variation of the cookie exists (ours if we set our cookie first), albeit with slightly different parameters than the ones they chose to give it. Since the site won't handle it, our extension needs to be vigilant in such cases and make sure to use the same settings of the site-assigned cookie. This is at least my thinking at the moment.
My only concern with this is that I believe the IAB protocol mentions only one cookie should be used by a site and a user to mutually exchange the opt-out information. This leads me to think if a user doesn't modify a site-provided IAB cookie, most site owners will not check for other variations of the cookie in the same way we do. Though this could be open to interpretation, I think I would prefer to keep only one IAB cookie per site for this reason. |
|
Here are some thoughts I have on a few rough ideas we could implement. Making a function to 'guess' what domain to use Creating cookies for each version of the |
|
Recent commit regarding multiple IAB cookies The big picture is that, if no cookie exists, we will place one. In the case of |
|
As discussed, @kalicki1 will continue with his testing (and possibly open new issues and close this one as the concrete work becomes more clear). In principle, there are two approaches:
|
|
Since I want to move development along in other areas of the extension and not spend too much time focused only on this issue, I will open a pull request to bring the changes made so far on this IAB CCPA implementation into the master branch. I will do the same with issue #42 to test the cookie-based code side by side and find ways to simplify the code base if possible. If major issues surface or revisions need to take place regarding this IAB spec implementation, I will open new, focused issues that address them specifically. Seeing as the major goal of this issue is now complete, we can close this issue as well. We can continue to use this issue as a reference to problems we resolved in the past if new issues in the IAB framework come up. |

Depending a bit on how things are developing on the policy end (i.e., whether we find some support for our signal, ideally in terms of standardization), we should consider also implementing the IAB CCPA Compliance Framework (should it turn out that there is not a whole lot of support for our signal). Their US Privacy String follows a similar idea as our signal, is technology-agnostic, and can be sent via a browser extension. It would be binding for companies participating in the IAB.
Here are some further references:
The text was updated successfully, but these errors were encountered: