The new deployment views across environments are now generally available (GA)!
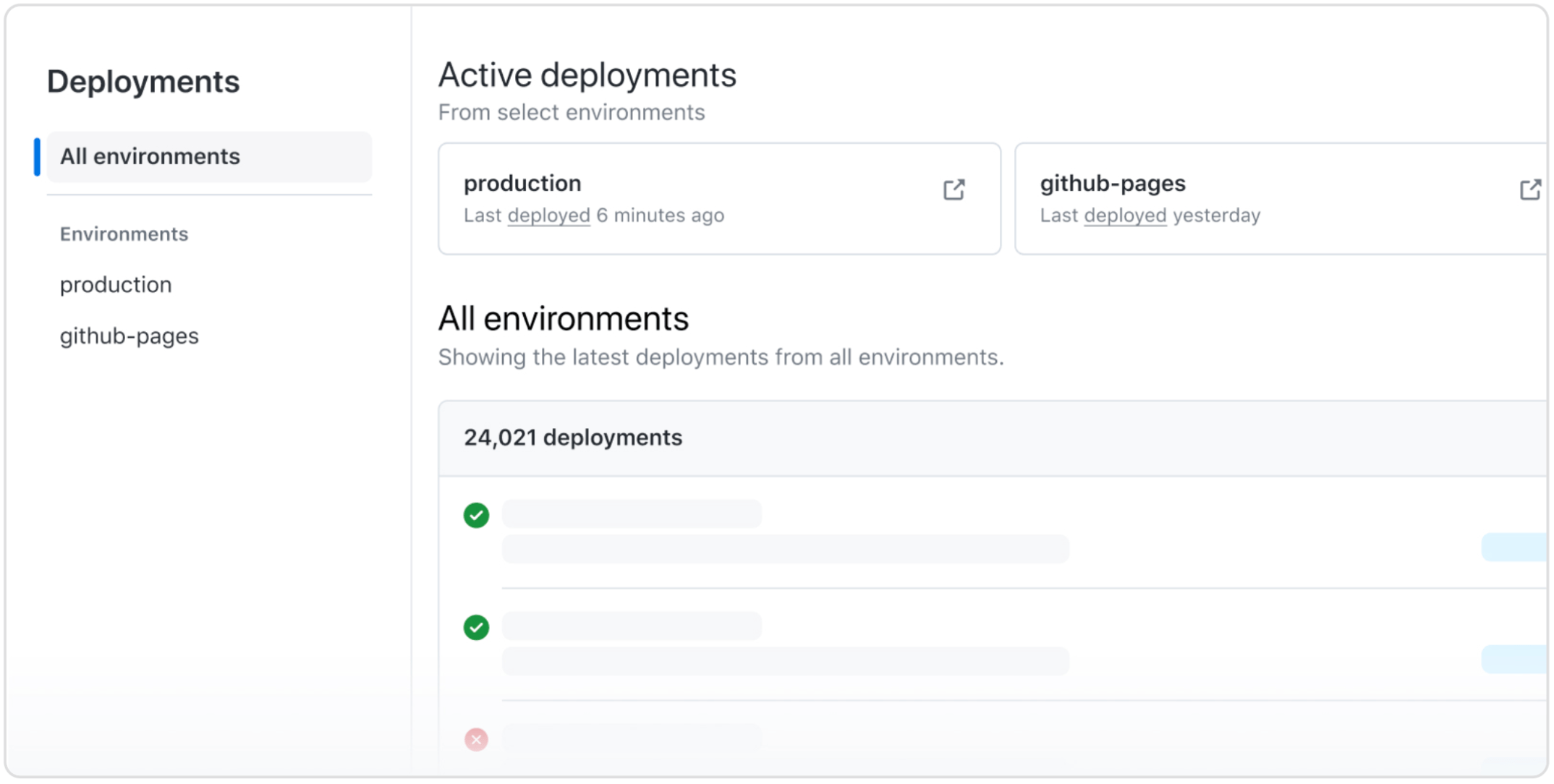
Previously we have shipped dashboard views to track your deployments using GitHub Actions across various environments.
These views have enabled Developers and DevOps managers to view the full history of deployments in a repository or filter them across environments & workflows to understand their status, duration or address any blockers.
We are now announcing GA for these Deployment Dashboard views along with the following enhancements:
- Pinning of environments. Ex: You can now “pin” up to 10 of your most critical environments to provide a quick way to view all the deployments rolled out to them.
- More filters on the views. Ex: You can now drill down to the list of deployments triggered by specific creators with specific deployment statuses and targeting specific environments.
Learn more about viewing and filtering deployments in your repository through our documentation.
For questions, visit the GitHub Actions community.
To see what’s next for Actions, visit our public roadmap.