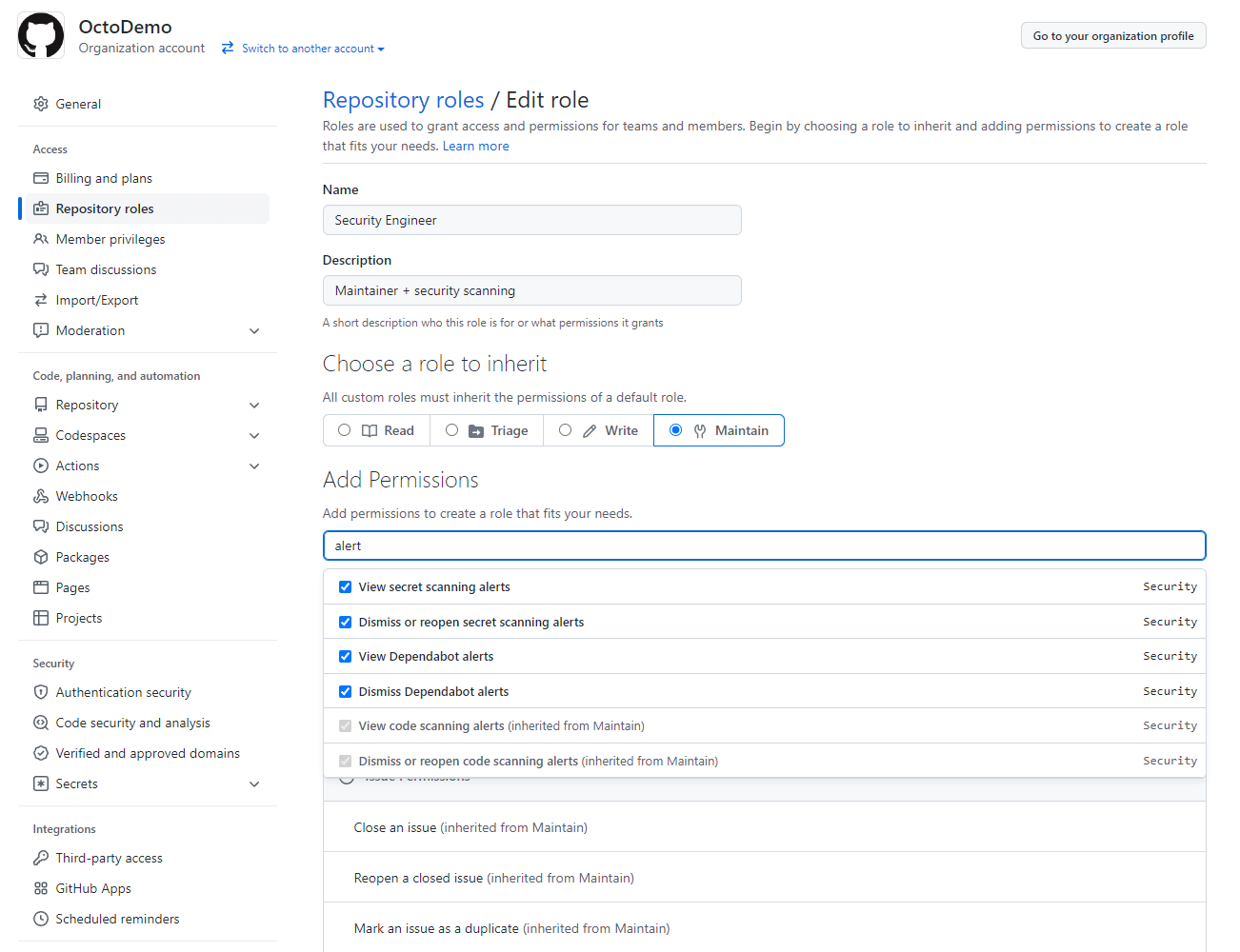
We’re excited to introduce enhancements to custom properties as well as updates to the push rule public beta.
Custom properties updates!
New property types
Multi selectallows a repo to have more than one value for a property defined. Now a repository can have a property that defines a compliance requirement with values for FedRamp and SOC2, for example.True/Falseallows you to set whether a given property is true or false for a given repository.
Target rulesets by repository visibility and more
In addition to targeting repositories with the custom properties you’ve created, we’ve now extended property targeting to include the ability to target by:
– Visibility: public, private, or internal
– Fork: true, false
– Language: select primary repository language.
Learn more in the custom properties documentation
What do you think? Start a discussion within GitHub Community.
Push rule delegated bypass public beta!
We are expanding on the push rule public beta with a new delegated bypass flow.
Previously to bypass push rules you had to be on the bypass list to push restricted content. Now with delegated bypass, contributors can propose bypassing a push rule and members of the bypass list can review those bypass requests to allow or deny the content.
Learn more about push rule delegated bypass in the repository rules documentation and join the push rule discussion in the GitHub Community.